SonicWall and Layer 3 Device configuration
So I'm tasked with creating inter VLAN routing but without having full access to our network. We are using a SonicWall routing device and about 12 Ubiquity EdgeSwitch devices. At first we were configuring our network to use VLANs for added security, but because we just had everything talking to each other over the SonicWall, it wasn't very secure and things were slow moving across the VLAN (the SonicWall was routing every packet).
We deal with big files (6gig to 36 gig files) and we have two locations connected via high speed wireless device with SonicWall routers on both ends. I've been working to move our actual routing to a core Layer 3 switch at each building to speed up file transfers that don't need to cross the wireless bridge. I have success in moving files within the switch, but the global gateway doesn't work (clients on a switch routed VLAN can't find the internet, only each other). I have my client gateways configure as the switch VLAN address and the switch global address set to an IP that is on the same subnet as the router. We've tried to configure a static route for each VLAN on the SonicWall pointing to this global switch gateway, but no dice.
The trunk global gateway is on a virtual interface. Our VLANs are configured on the SonicWall with virtual interfaces. I don't know if these virtual interfaces are causing an issue with the VLAN routing packets BACK to the switch or not. I can ping anything in our building on any client connected to a routed VLAN, but it will not reach anything in the WAN.
Is there a step I'm missing with correctly creating a static route on a SonicWall router to enable a switch to perform Layer 3 actions to speed up file transfer? The core switch is moving files around 2 Gp/s over a LAG where as before I was lucky to get 500 Mp/s so it's half working. Thanks for the help.
Best Answer
-
CORRECT ANSWER
 Ajishlal
Community Legend ✭✭✭✭✭
Ajishlal
Community Legend ✭✭✭✭✭
Hi @Nick_S ,
I am also having same kind of the Network infra but I configured in the L3 switch " Default Routing to the Firewall X0 IP" For example: "ip route 0.0.0.0 0.0.0.0 10.10.55.1"
All VLAN's are created in Core switch & not created any VLAN interface in Sonicwall.
Sonicwall X0 interface (LAN) configured with 10.10.55.1/24
SonicWALL Configuration:
1) Create address object for the VLAN's & Create address object group for the created VLAN address object and added in the Group.
2) Created address object for "VLAN Gateway":
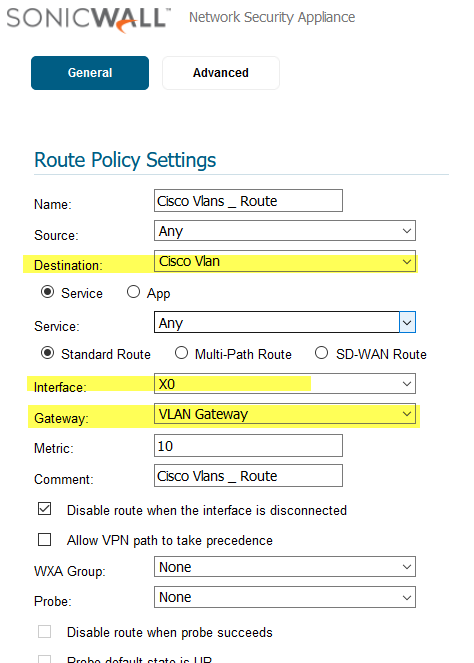
3) Created Static Routing in SonicWALL:
Network Diagram: In this scenario all Internal traffic handled by the core switch and Sonicwall will do the Internet Traffic for the all VLAN'S.
Let me know if this would help you to resolve your issue.
7





Answers
Hello @Nick_S,
Welcome to SonicWall community.
If you are using an L3 switch on X0:V55, you would need the following on the SonicWall.
1) A VLAN sub-interface with VLAN ID 55 and IP on the same subnet as the switch
2) Static routes that say 10.10.20.0/24 and 10.10.80.0/24 can be reached via gateway 10.10.56.6
On the switch you should have the default gateway as the firewall which is 10.10.56.1.
If the traffic generated from those internal networks still cannot reach the internet, please check if the access rules are blocking them from LAN to WAN.
You can perform a packet capture while you ping 8.8.8.8 or any WAN address from those internal machines to understand what may be taking place.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
If I read this configuration right, you had one static route that took care of all internet traffic for all the VLANs? My current (mostly working) set up has a unique static route per vlan and I still can't get all WAN traffic to work. Many sites report "can't establish a secure connection" on browsers.
For example, my destination is the ip of the VLAN interface on the core switch. 10.10.20.4 for instance. Where is your destination going to? That might be a feature of a Cisco switch, we are using Edge Switches by Ubiquity. Thank you for your very helpful response, this did help me get some bugs worked out.
Sorry about bringing up an old thread, but this is exactly what I am trying to do as well. Is the VLAN 55 in the diagram the management VLAN?
Mikew1102 - Yes...in that diagram we were using VLAN 55 as the management VLAN.