NAT Policies
I read in the documentation that SonicOS creates a default outgoing NAT policy for each interface configured. Looking at our NAT policies, we have quite a few default policies.
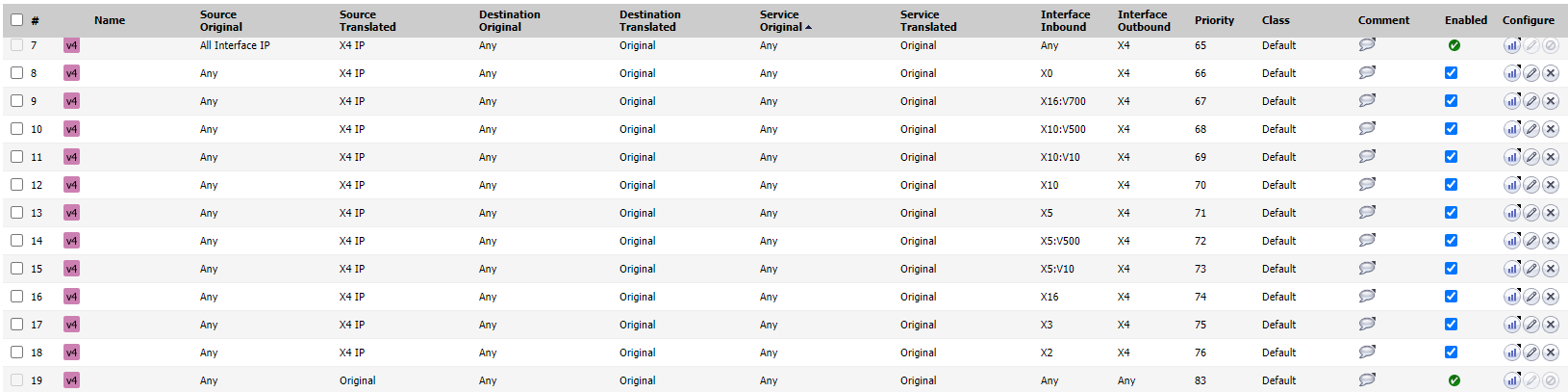
Attached is a screenshot of some of the ones I'm curious about. In the pic, the top and the bottom one appear that they cannot be disabled.
The top one reads "Auto added X4 default NAT policy." This is our WAN interface.
The bottom one reads "Default NAT policy".
Why are these one not able to be disabled and why is there a "default NAT policy" if a default policy is automatically created for each configured interface anyways?
Category: High End Firewalls
0


Answers
Hello @djhurt1 ,
The SonicWall adds default NAT policy for each WAN interface from each internal interface. This allows all internal subnets to go online using the WAN address of the firewall - Rules 8 through 18
The first one in the image you have attached, is for the Firewall Interface IPs to use the WAN Interface IP - X4 IP when connecting to the internet. This is useful for license sync, signature downloads etc.
The last rule in this list is a 'No NAT' which is given the least priority. When none of the other NAT policies match, it uses the No NAT so that no changes are made to the IP packet.
If you have any further queries, let me know.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
Hi @djhurt1 ,
The default Nat policies and rules cannot be disabled or edited until we have a specific setting enabled on the DIAG page because these are highly sensitive policies needed for the network to go online. By mistake if some policies are changed or deleted that might affect the production.
Hope this helps.
Do let us know if you have any queries.
Thanks & Regards,
Poornima.T.R
@djhurt1 ,
I believe the firewall has the option enabled. The default NAT rules on the firewall cannot be edited until we have the option enabled on the diag page "Enable the ability to disable auto-added NAT policy".
If the option is disabled, then we will see all the default NAT polices as below:
Nevyaditha P
Technical Support Advisor, Premier Services
In order to disable do as per:
https://www.sonicwall.com/support/knowledge-base/how-to-disable-auto-added-nat-policies-in-gen-6-sonicos/170504652112814
Be wary though as the SonicWALLs tend to reapply "Auto" rules such as NAT and Access rules when you either reboot on some firmwares or when you are making a config change which on apply will "auto add" a rule, such as VPN. So I found the best bet is to disable the auto rules instead of delete, when you delete they get recreated.
For the 2 NAT rules you pointed out, the first NAT is on the actual sonicwall interface IP's outbound to the internet via X4, not the LAN subnets, a failsafe rule I would imagine.
The last rule is your No-Nat rule, such as between your internal lan subnets/zones.
If I need to create a specific 1:1 NAT rule, do I just edit the automatically created NAT rule or do I create a separate rule and give it higher priority? I know it's a simple question but trying to get a firm grasp on how SonicOS works.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
Create a new one, what are you looking to do exactly? If you are looking to publish a service to the internet for example you can use the "wizard/quick configuration" button to generate the NAT and rules you need, then take a look at what was created to understand it.
The wizard/quick config will create more than you need and can name the objects (network and service) it creates in a slightly annoying way but you can rename them after. I think this is the best way to learn what to do and then after you are comfortable you can manually do it (which is the better way to do it for complete oversight).