IPSEC tunnel with multiple destination networks
in SSL VPN
Hi. I have configured a site to site IPSec tunnel. It works fine with one destination network (10.88.88.0/24 or 10.99.99.0/24) without changing the other end configuration but not with both in the same time : only one gets active.
Any ideas?
Best Regards,
Category: SSL VPN
0


Answers
@pe_pips_988,
Welcome to the SonicWall community.
What device is being used as the peer VPN device? Please make sure that they are not using tunnel mode VPN whereas this is a site to site policy mode of the VPN.
You can try using tunnel mode VPN and create routing policies and test if that works.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
Thanks for your input. Peer VPN device is PFSense (see config attached). Does it help?
Best Regards,
@pe_pips_988,
The mode does show up as tunnel but I am not sure if they use different terminology. Please use the following KB article and use the route-based VPN setup.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
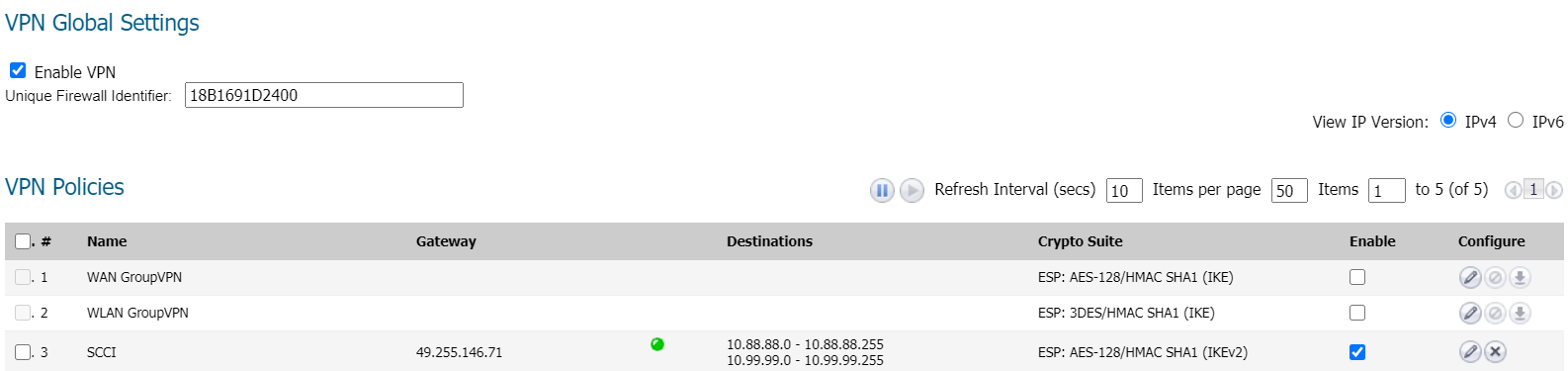
Tunnel in PFsense is site to site. This configuration works fine if I enable only 10.88.88.0/24 child or 10.99.99.0/24 child in phase 2 but not both in the same time.
I have tried route-base VPN setup without success.
See below log summary. Negociation for 10.88.88.0/24 child is OK (green circled) but it looks like the second one for 10.99.99.0/24 fails (red circled)
and the PFSense logs just when I'm starting the VPN
Feb 16 23:32:21 charon 08[IKE] <con2000|31> nothing to initiate
Feb 16 23:32:21 charon 08[IKE] <con2000|31> activating new tasks
Feb 16 23:32:21 charon 08[NET] <con2000|31> sending packet: from 49.255.146.71[4500] to 52.62.1.159[4500] (92 bytes)
Feb 16 23:32:21 charon 08[ENC] <con2000|31> generating INFORMATIONAL_V1 request 2625719872 [ HASH N(DPD_ACK) ]
Feb 16 23:32:21 charon 08[IKE] <con2000|31> activating ISAKMP_DPD task
Feb 16 23:32:21 charon 08[IKE] <con2000|31> activating new tasks
Feb 16 23:32:21 charon 08[IKE] <con2000|31> queueing ISAKMP_DPD task
Feb 16 23:32:21 charon 08[ENC] <con2000|31> parsed INFORMATIONAL_V1 request 1741804763 [ HASH N(DPD) ]
Feb 16 23:32:21 charon 08[NET] <con2000|31> received packet: from 52.62.1.159[4500] to 49.255.146.71[4500] (92 bytes)
Feb 16 23:32:17 charon 08[IKE] <con1000|30> nothing to initiate
Feb 16 23:32:17 charon 08[IKE] <con1000|30> activating new tasks
Feb 16 23:32:17 charon 08[NET] <con1000|30> sending packet: from 49.255.146.71[4500] to 3.104.98.85[4500] (92 bytes)
Feb 16 23:32:17 charon 08[ENC] <con1000|30> generating INFORMATIONAL_V1 request 3582485950 [ HASH N(DPD_ACK) ]
Feb 16 23:32:17 charon 08[IKE] <con1000|30> activating ISAKMP_DPD task
Feb 16 23:32:17 charon 08[IKE] <con1000|30> activating new tasks
Feb 16 23:32:17 charon 08[IKE] <con1000|30> queueing ISAKMP_DPD task
Feb 16 23:32:17 charon 08[ENC] <con1000|30> parsed INFORMATIONAL_V1 request 3186740057 [ HASH N(DPD) ]
Feb 16 23:32:17 charon 08[NET] <con1000|30> received packet: from 3.104.98.85[4500] to 49.255.146.71[4500] (92 bytes)
Feb 16 23:32:16 charon 08[IKE] <con3000|113> nothing to initiate
Feb 16 23:32:16 charon 08[IKE] <con3000|113> activating new tasks
Feb 16 23:32:16 charon 08[ENC] <con3000|113> parsed INFORMATIONAL response 0 [ ]
Feb 16 23:32:16 charon 08[NET] <con3000|113> received packet: from 202.22.228.44[500] to 49.255.146.71[500] (60 bytes)
Feb 16 23:32:16 charon 08[NET] <con3000|113> sending packet: from 49.255.146.71[500] to 202.22.228.44[500] (60 bytes)
Feb 16 23:32:16 charon 08[ENC] <con3000|113> generating INFORMATIONAL request 0 [ ]
Feb 16 23:32:16 charon 08[IKE] <con3000|113> activating IKE_DPD task
Feb 16 23:32:16 charon 08[IKE] <con3000|113> activating new tasks
Feb 16 23:32:16 charon 08[IKE] <con3000|113> queueing IKE_DPD task
Feb 16 23:32:16 charon 08[IKE] <con3000|113> sending DPD request
Feb 16 23:32:11 charon 08[IKE] <con2000|31> nothing to initiate
Feb 16 23:32:11 charon 08[IKE] <con2000|31> activating new tasks
Feb 16 23:32:11 charon 08[NET] <con2000|31> sending packet: from 49.255.146.71[4500] to 52.62.1.159[4500] (92 bytes)
Feb 16 23:32:11 charon 08[ENC] <con2000|31> generating INFORMATIONAL_V1 request 3537275143 [ HASH N(DPD_ACK) ]
Feb 16 23:32:11 charon 08[IKE] <con2000|31> activating ISAKMP_DPD task
Feb 16 23:32:11 charon 08[IKE] <con2000|31> activating new tasks
Feb 16 23:32:11 charon 08[IKE] <con2000|31> queueing ISAKMP_DPD task
Feb 16 23:32:11 charon 08[ENC] <con2000|31> parsed INFORMATIONAL_V1 request 1638335053 [ HASH N(DPD) ]
Feb 16 23:32:11 charon 08[NET] <con2000|31> received packet: from 52.62.1.159[4500] to 49.255.146.71[4500] (92 bytes)
Feb 16 23:32:07 charon 08[IKE] <con1000|30> nothing to initiate
Feb 16 23:32:07 charon 08[IKE] <con1000|30> activating new tasks
Feb 16 23:32:07 charon 08[NET] <con1000|30> sending packet: from 49.255.146.71[4500] to 3.104.98.85[4500] (92 bytes)
Feb 16 23:32:07 charon 08[ENC] <con1000|30> generating INFORMATIONAL_V1 request 3732169982 [ HASH N(DPD_ACK) ]
Feb 16 23:32:07 charon 08[IKE] <con1000|30> activating ISAKMP_DPD task
Feb 16 23:32:07 charon 08[IKE] <con1000|30> activating new tasks
Feb 16 23:32:07 charon 08[IKE] <con1000|30> queueing ISAKMP_DPD task
Feb 16 23:32:07 charon 08[ENC] <con1000|30> parsed INFORMATIONAL_V1 request 3656883096 [ HASH N(DPD) ]
Feb 16 23:32:07 charon 08[NET] <con1000|30> received packet: from 3.104.98.85[4500] to 49.255.146.71[4500] (92 bytes)
Feb 16 23:32:06 charon 08[NET] <con3000|113> sending packet: from 49.255.146.71[500] to 202.22.228.44[500] (68 bytes)
Feb 16 23:32:06 charon 08[ENC] <con3000|113> generating CREATE_CHILD_SA response 2 [ N(NO_PROP) ]
Feb 16 23:32:06 charon 08[CHD] <con3000|113> CHILD_SA con3000{1485} state change: CREATED => DESTROYING
Feb 16 23:32:06 charon 08[IKE] <con3000|113> failed to establish CHILD_SA, keeping IKE_SA
Feb 16 23:32:06 charon 08[IKE] <con3000|113> no acceptable proposal found
Feb 16 23:32:06 charon 08[CFG] <con3000|113> configured proposals: ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ
Feb 16 23:32:06 charon 08[CFG] <con3000|113> received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Feb 16 23:32:06 charon 08[CFG] <con3000|113> no acceptable DIFFIE_HELLMAN_GROUP found
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selecting proposal:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> found matching child config "con3000" with prio 6
Feb 16 23:32:06 charon 08[CFG] <con3000|113> candidate "con3000" with prio 5+1
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 192.168.0.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> proposing traffic selectors for other:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 10.99.99.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 10.88.88.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> proposing traffic selectors for us:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> looking for a child config for 10.99.99.0/24|/0 === 0.0.0.0/0|/0
Feb 16 23:32:06 charon 08[ENC] <con3000|113> parsed CREATE_CHILD_SA request 2 [ SA No TSi TSr ]
Feb 16 23:32:06 charon 08[NET] <con3000|113> received packet: from 202.22.228.44[500] to 49.255.146.71[500] (172 bytes)
Feb 16 23:32:06 charon 08[NET] <con3000|113> sending packet: from 49.255.146.71[500] to 202.22.228.44[500] (212 bytes)
Feb 16 23:32:06 charon 08[ENC] <con3000|113> generating IKE_AUTH response 1 [ IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(AUTH_LFT) ]
Feb 16 23:32:06 charon 08[CHD] <con3000|113> CHILD_SA con3000{1484} state change: INSTALLING => INSTALLED
Feb 16 23:32:06 charon 08[IKE] <con3000|113> CHILD_SA con3000{1484} established with SPIs c583428b_i 4fe8130c_o and TS 10.88.88.0/24|/0 === 192.168.0.0/24|/0
Feb 16 23:32:06 charon 08[CHD] <con3000|113> SPI 0x4fe8130c, src 49.255.146.71 dst 202.22.228.44
Feb 16 23:32:06 charon 08[CHD] <con3000|113> adding outbound ESP SA
Feb 16 23:32:06 charon 08[CHD] <con3000|113> SPI 0xc583428b, src 202.22.228.44 dst 49.255.146.71
Feb 16 23:32:06 charon 08[CHD] <con3000|113> adding inbound ESP SA
Feb 16 23:32:06 charon 08[CHD] <con3000|113> using HMAC_SHA1_96 for integrity
Feb 16 23:32:06 charon 08[CHD] <con3000|113> using AES_CBC for encryption
Feb 16 23:32:06 charon 08[CHD] <con3000|113> CHILD_SA con3000{1484} state change: CREATED => INSTALLING
Feb 16 23:32:06 charon 08[CFG] <con3000|113> config: 192.168.0.0/24|/0, received: 0.0.0.0/0|/0 => match: 192.168.0.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selecting traffic selectors for other:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> config: 10.99.99.0/24|/0, received: 10.88.88.0/24|/0 => no match
Feb 16 23:32:06 charon 08[CFG] <con3000|113> config: 10.88.88.0/24|/0, received: 10.88.88.0/24|/0 => match: 10.88.88.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selecting traffic selectors for us:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Feb 16 23:32:06 charon 08[CFG] <con3000|113> configured proposals: ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ
Feb 16 23:32:06 charon 08[CFG] <con3000|113> received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Feb 16 23:32:06 charon 08[CFG] <con3000|113> proposal matches
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selecting proposal:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> found matching child config "con3000" with prio 6
Feb 16 23:32:06 charon 08[CFG] <con3000|113> candidate "con3000" with prio 5+1
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 192.168.0.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> proposing traffic selectors for other:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 10.99.99.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> 10.88.88.0/24|/0
Feb 16 23:32:06 charon 08[CFG] <con3000|113> proposing traffic selectors for us:
Feb 16 23:32:06 charon 08[CFG] <con3000|113> looking for a child config for 10.88.88.0/24|/0 === 0.0.0.0/0|/0
Feb 16 23:32:06 charon 08[IKE] <con3000|113> maximum IKE_SA lifetime 28729s
Feb 16 23:32:06 charon 08[IKE] <con3000|113> scheduling reauthentication in 28189s
Feb 16 23:32:06 charon 08[IKE] <con3000|113> IKE_SA con3000[113] state change: CONNECTING => ESTABLISHED
Feb 16 23:32:06 charon 08[IKE] <con3000|113> IKE_SA con3000[113] established between 49.255.146.71[49.255.146.71]...202.22.228.44[202.22.228.44]
Feb 16 23:32:06 charon 08[IKE] <con3000|113> successfully created shared key MAC
Feb 16 23:32:06 charon 08[IKE] <con3000|113> authentication of '49.255.146.71' (myself) with pre-shared key
Feb 16 23:32:06 charon 08[IKE] <con3000|113> authentication of '202.22.228.44' with pre-shared key successful
Feb 16 23:32:06 charon 08[CFG] <con3000|113> selected peer config 'con3000'
Feb 16 23:32:06 charon 08[CFG] <113> ignore candidate 'bypasslan' without matching IKE proposal
Feb 16 23:32:06 charon 08[CFG] <113> candidate "con3000", match: 1/20/3100 (me/other/ike)
Feb 16 23:32:06 charon 08[CFG] <113> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 16 23:32:06 charon 08[CFG] <113> looking for peer configs matching 49.255.146.71[%any]...202.22.228.44[202.22.228.44]
Feb 16 23:32:06 charon 08[IKE] <113> received 3 cert requests for an unknown ca
Feb 16 23:32:06 charon 08[IKE] <113> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd
Feb 16 23:32:06 charon 08[IKE] <113> received cert request for unknown ca with keyid f2:98:d3:e8:75:f1:24:da:18:04:f4:c4:1c:9f:b0:84:f2:d5:58:9c
Feb 16 23:32:06 charon 08[IKE] <113> received cert request for unknown ca with keyid 51:bc:4f:77:17:08:cf:e5:09:dd:e9:ea:a5:54:8e:91:c0:67:78:53
Feb 16 23:32:06 charon 08[ENC] <113> parsed IKE_AUTH request 1 [ IDi CERTREQ AUTH SA TSi TSr N(INIT_CONTACT) ]
Feb 16 23:32:06 charon 08[NET] <113> received packet: from 202.22.228.44[500] to 49.255.146.71[500] (260 bytes)
Feb 16 23:32:06 charon 08[NET] <113> sending packet: from 49.255.146.71[500] to 202.22.228.44[500] (316 bytes)
Feb 16 23:32:06 charon 08[ENC] <113> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(CHDLESS_SUP) N(MULT_AUTH) ]
Feb 16 23:32:06 charon 08[CFG] <113> selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 16 23:32:06 charon 08[CFG] <113> configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 16 23:32:06 charon 08[CFG] <113> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 16 23:32:06 charon 08[CFG] <113> proposal matches
Feb 16 23:32:06 charon 08[CFG] <113> selecting proposal:
Feb 16 23:32:06 charon 08[IKE] <113> IKE_SA (unnamed)[113] state change: CREATED => CONNECTING
Feb 16 23:32:06 charon 08[IKE] <113> 202.22.228.44 is initiating an IKE_SA
@pe_pips_988,
The red log shows that the peer is notifying about an error in the payload. I could not find any reported issues like this, but I think it would be best to work on this over a support ticket.
One last thing though, right now who is the initiator, SonicWall or PF sense? Could you reverse the keep alive and test once?
Thank you!
Shipra Sahu
Technical Support Advisor, Premier Services
Thanks for letting us know. Glad that it is all fixed now!
Shipra Sahu
Technical Support Advisor, Premier Services