AWS VPN Problem with 6.5.4.6-79n
 JeffW
Newbie ✭
JeffW
Newbie ✭
Has anyone here successfully set up the AWS VPN on the Sonicwall 2600? I set it up on 2 different units and get all green lights on the VPN sessions, yet I can't connect/ping to the AWS Instance nor connect/ping to my internal client box using the Sonicwall as a gateway. The Security Group has an entry to allow ALL traffic from my internal LAN. The firmware being used (apparently important in this case) is 6.5.4.6-79n. I will include pics of the relevant screens on the 2600 for reference. Thanks in advance.
Best Answers
-
CORRECT ANSWER
 shiprasahu93
Moderator
shiprasahu93
Moderator
Hello @JeffW,
Welcome to SonicWall community.
The VPN seems to be up and running. You can run a continuous ping to the internal client box behind AWS from your internal LAN and then perform a packet capture to see if the return traffic is even sent to us or if it is coming on the wrong interface. Sometimes, especially with AWS, it performs load balancing on AWS side where the traffic is sent from the first VPN and the return traffic comes from the second VPN.
If that's the case, you can enable asymmetric routing option under the advanced tab of the VPN tunnel interfaces.
I hope this helps!
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
6 -
CORRECT ANSWER
 JeffW
Newbie ✭
JeffW
Newbie ✭
Fixed. Turns out it was a metric issue in the Routing Policy. It was set by the AWS VPN wizard as 1, and the amazing tech Pooja Singh set it to 6 and viola...we had connectivity. Picture attached.
0 -
CORRECT ANSWER
 JeffW
Newbie ✭
JeffW
Newbie ✭
The above "fix" did not work after reboot, so here is the final fix (essentially a better keep-alive) to this issue, courtesy of the great tech.
His notes:
-Route policies show greyed-out
-VPN was up
-any change on tunnel interface will pass the traffic and routes will come alive
-enabled asymmetric route , traffic passed but after reboot again same issue
-changed the zone address object of AWS network from LAN to VPN
-traffic passed
-restarted the firewall
-again routes were not working
-created Network probe but source as X0 Ip address and destination as AWS server and it went green but routes were still grayed out
-pushed the probe in routes and that fixed the issue
After reboot it was still working
0


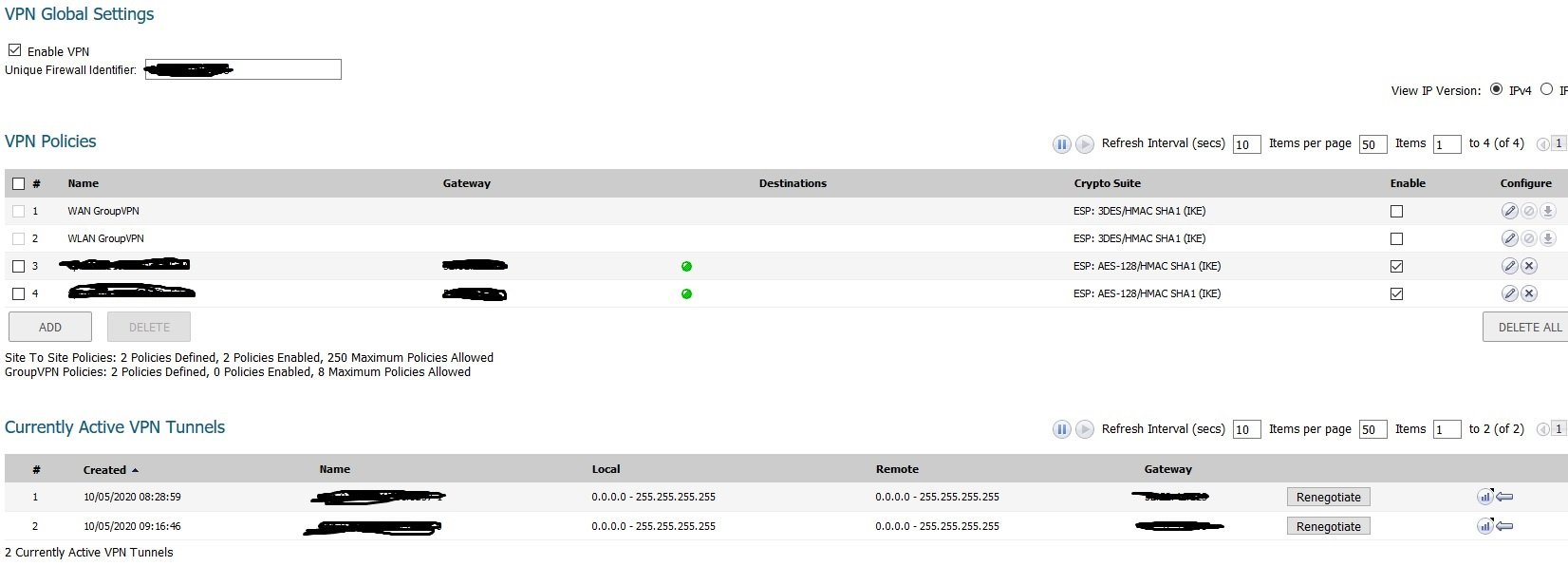

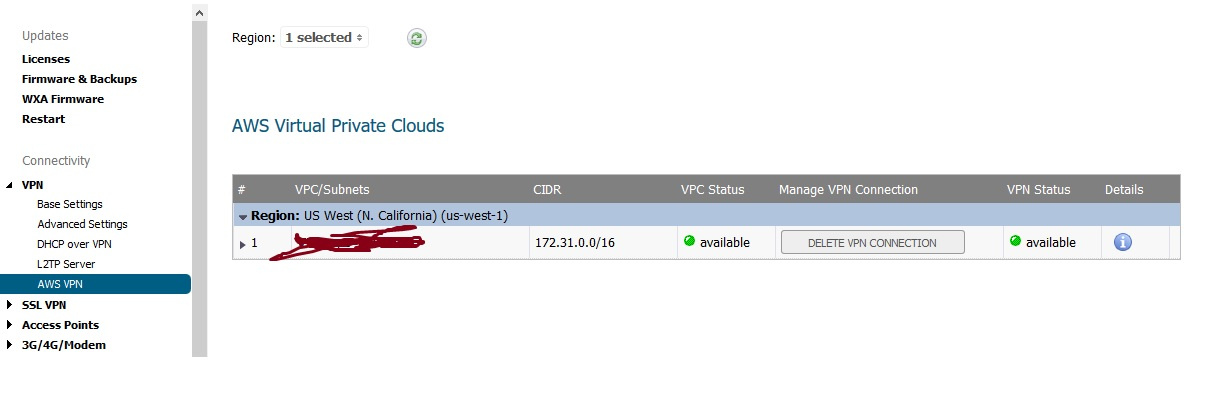



Answers
Thanks for the reply. I enabled that feature on both VPN tunnels and can now ping from the Instance to my LAN host, but not the other way around. I will investigate the packet log.
Sure. Let us know how it goes.
Shipra Sahu
Technical Support Advisor, Premier Services
Working with an AWS tech, he noticed that the ICMP packets were not being routed via the vpn tunnel interface, but instead were being sent to the WAN interface X0. Any idea how to fix this issue?
172.16.0.71 LAN client
172.31.11.254 AWS Instance
Working session:
==========
*Packet number: 218*
Header Values:
Bytes captured: 74, Actual Bytes on the wire: 74
Packet Info(Time:10/07/2020 10:33:29.592):
in:--, out:T_vpn_077485c77318fe435_0*, Consumed, Module Id:20, 2:2)
Ethernet Header
Ether Type: IP(0x800), Src=[c0:ea:e4:86:5a:ef], Dst=[c0:ea:e4:86:5a:ee]
IP Packet Header
IP Type: ICMP(0x1), Src=[172.16.0.71], Dst=[172.31.11.254]
ICMP Packet Header
ICMP Type = 8(ECHO_REQUEST), ICMP Code = 0, ICMP Checksum = 18849
Value:[1]
Hex and ASCII dump of the packet:
c0eae486 5aeec0ea e4865aef 08004500 003cd931 00008001 *....Z.....Z...E..<.1....*
fd1aac10 0047ac1f 0bfe0800 49a10001 03ba6162 63646566 *.....G......I.....abcdef*
6768696a 6b6c6d6e 6f707172 73747576 77616263 64656667 *ghijklmnopqrstuvwabcdefg*
6869 *hi *
Non-working one:
==============
*Packet number: 901*
Header Values:
Bytes captured: 74, Actual Bytes on the wire: 74
Packet Info(Time:10/07/2020 11:04:16.064):
in:--, out:X1*, Forwarded, 2:2)
Ethernet Header
Ether Type: IP(0x800), Src=[c0:ea:e4:86:5a:ef], Dst=[00:00:de:af:03:00]
IP Packet Header
IP Type: ICMP(0x1), Src=[174.79.116.58], Dst=[172.31.11.254]
ICMP Packet Header
ICMP Type = 8(ECHO_REQUEST), ICMP Code = 0, ICMP Checksum = 50237
Value:[0]
Hex and ASCII dump of the packet:
0000deaf 0300c0ea e4865aef 08004500 003cd9c8 00008001 *..........Z...E..<......*
8651ae4f 743aac1f 0bfe0800 c43d84ef 042f6162 63646566 *.Q.Ot:.......=.../abcdef*
6768696a 6b6c6d6e 6f707172 73747576 77616263 64656667 *ghijklmnopqrstuvwabcdefg*
6869 *hi *
This issue seems relevant.
https://www.sonicwall.com/support/knowledge-base/site-to-site-vpn-tunnel-is-up-but-only-passing-traffic-in-one-direction/170503745701929/#:~:text=If%20the%20packets%20are%20marked%20as%20Consumed%20then,translation%20policies%2C%20which%20could%20lead%20to%20incorrect%20routing.
Hello @JeffW,
Could you please make sure that the necessary route policies for AWS VPN are in place? If yes, kindly reach out to our support team for real-time troubleshooting.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
Perfect. Glad to know that the issue is taken care of. Have a good one!
Shipra Sahu
Technical Support Advisor, Premier Services