VPN NETWORK OVERLAPPING PROBLEM (at source)
 SEBASTIAN
Newbie
SEBASTIAN
Newbie
Hi everybody! I hope you are all fine!
I have this problem now with a customer of us.
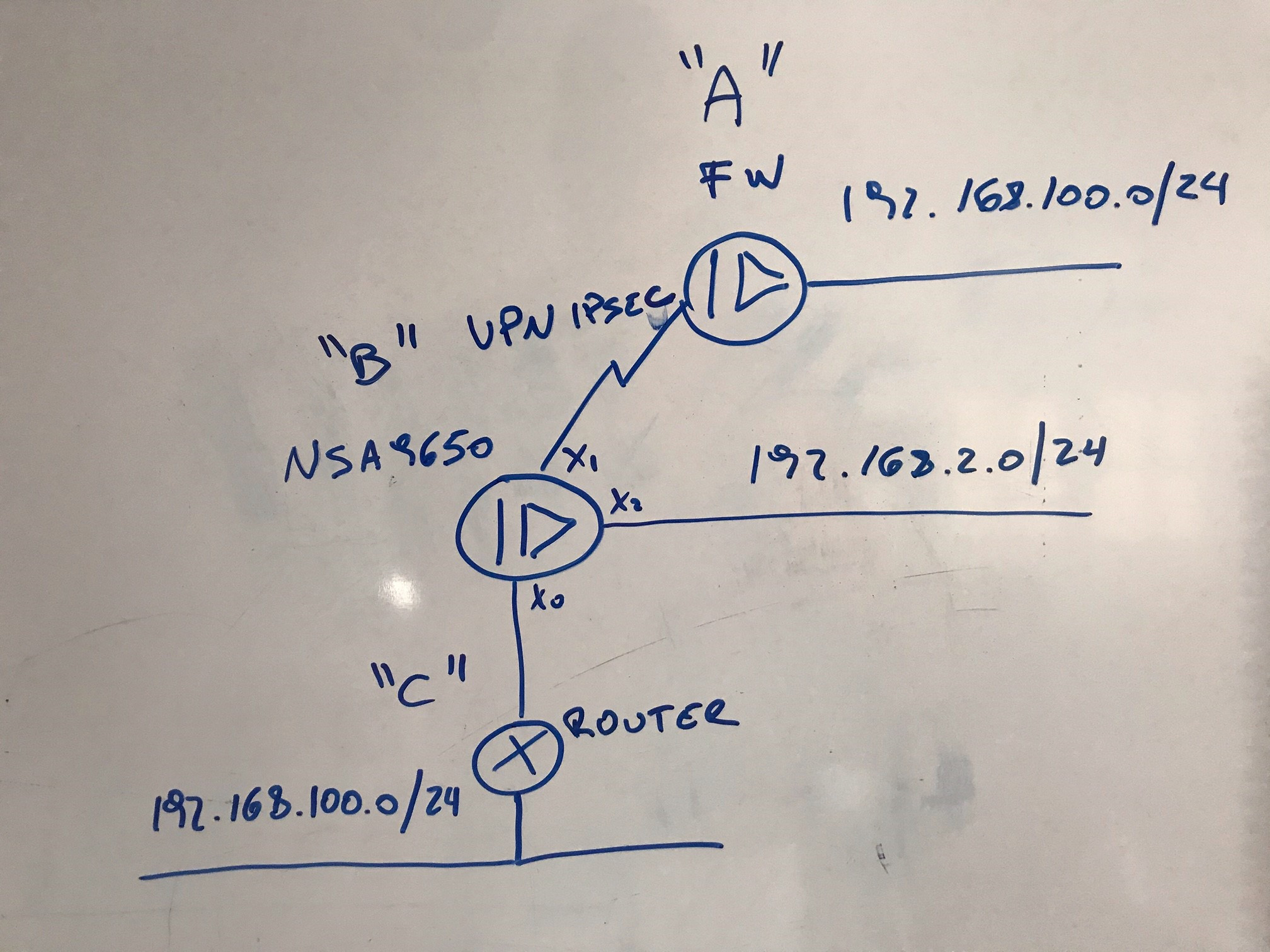
We have an IPSEC VPN (main mode) between site "A" and site "B". This is the only way we can configure the VPN since it is not allowed to touch firewall at site "A". We are not allowed to change anything at site "A".
We need to communicate from network 192.168.2.0/24 to network 192.168.100.0/24 through the VPN.
But communication is going down to router at site "C". This is normal because we have a static route on NSA9650 that says so.
Is there any possibility to force communication between network 192.168.2.0/24 and network 192.168.100.0/24 on site "A" go through the VPN?
I tried it with a policy route, but when the VPN goes down and then up, the policy appears deactivated.


Answers
The route policy takes effect because it has more priority than the VPN. Is there any possibility that you could use tunnel interface VPN?
Regards
Saravanan V
Technical Support Advisor - Premier Services
Professional Services
Hi @Saravanan,
I cannot touch configuration on the other site of the VPN.
@SEBASTIAN
are you going to different host IP addresses across the vpn compared to the Static routed network, for example are they unique IP addresses that you have to contact on the VPN side which aren't configured on the Static route or are you trying to communicate to an IP over the VPN on 192.168.100.5 for example and the same IP address is configured on a device via the static route?
If they are unique IP addresses that you are trying to access across the VPN you can put in a range or indididual IP addreses in the Route policies, the more specific you make the route policy the better the priority also.
or you could do the opposite, so if you only need to contact certain IP addreses on the staic route network, create the ranges/hosts and put them in a group and only have them as the destination on the Internal static route
Just to clarify you cannot use Ranges in the VPN policy, only on the PBR
Hope all that made sense
Hi @preston
I think I see your point.
I have to reach just an IP address 192.168.100.100 through the VPN.
And the NSA9650 has a static route to reach the hole 192.168.100.0/24 network through the router at "C".
The problem I see is the VPN is in "main mode", not "tunnel mode". So I cannot configure any specific route policy.
Hi Sebastian,
I understand you have no way of modifying the configuration on Site A.
I can't think of anything apart from changing the subnet on Site C or perform NAT masking on Site C router for 192.168.100.x/24. If its the VPN tunnel running between Site B and Site C, then we would have got an option of performing NAT over VPN but we are unfortunate on this part.
Regards
Saravanan V
Technical Support Advisor - Premier Services
Professional Services
Hi @Saravanan
I agree with you. I am trying to explain this scenario to the customer.
They are going to ask their Data Center tech guys one more time the possibility to change the config on site "A".
I do not see any other chance to solve this.
Thanks!
Yes, exactly. You are right @SEBASTIAN.
Regards
Saravanan V
Technical Support Advisor - Premier Services
Professional Services
Hi @SEBASTIAN
If you only have to reach the one IP address over the VPN, change your static route to the 192.168.100.0 to use two IP ranges instead one for 192.168.100.1-99 then another for 192.168.101-192.168.100.254 put them in a group and then change as the destination on the route policy for the Internal route , then see if you can get to 192.168.100.100
@Saravanan
In that case I could do NAT over IPSEC on their firewall, or I could do "Numbered Tunnel Interface VPN (Route-Based VPN)".
Thanks,
Hi @SEBASTIAN
not sure if you saw my latest reply
@preston
That is a good one. I just need to be sure 192.168.100.100 is not being used.
I will have a try and let you know if it worked.
Thanks,
You are right again @SEBASTIAN.
Regards
Saravanan V
Technical Support Advisor - Premier Services
Professional Services
Hi @preston
I did it as you said.
It seems to be working fine for all protocols between 192.168.2.0/24 and 192.168.100.100/32.
But, there is always a "but" in IT!!!
I did a "tracert" to realize PING from 192.168.2.0/24 to 192.168.100.100/32 is going through Internet and not through VPN.
If I stop PING and wait for some seconds, then, the PING responds from 192.168.100.100/32.
HI @SEBASTIAN
can you access what you were trying to access then on 192.168.100.100?
it usually shows the traffic for a VPN going over X1 rather than X0 , it would be impossible to get to 192.168.100.100 over the Internet as it is a non routable subnet, what does it show in the sonicwall packet monitor?
Hi @preston ,
Yes, now I can access to a service on 192.168.100.100.
But PING, that is trying to go through X1 (WAN Internet).
Hi @SEBASTIAN
if you do a packet trace for ICMP on the Sonicwall going to 192.168.100.100 what is it saying?