Tech Tips: DECRYPTING VPN TRAFFIC USING WIRESHARK
 Nevyaditha
Moderator
Nevyaditha
Moderator
Encryption is the process of encoding data so that only a computer with the right decoder will be able to read and use it.
The VPN client at each end of the tunnel encrypt the data entering the tunnel and decrypt it at the other end. There are most two common forms of encryption symmetric-key encryption and public-key Encryption. Encryption and decryption will be handled by the VPN terminating devices it can be Firewalls or Routers.
Below Is the way in which ESP traffic can be decrypted via Wireshark (Tool to Capture packets).
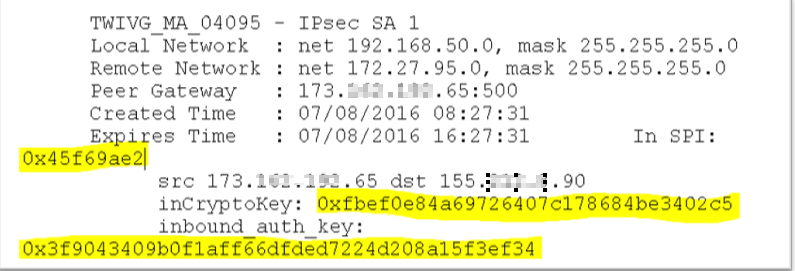
1. Copy the source and destination public IPs for which you need to decrypt the traffic from Wireshark. Here 173.162.192.65 is the IP of remote firewall (Not a SonicWALL ) and 155.212.8.90 is the IP of local firewall ( IP of SonicWALL).
2. In the TSR of SonicWALL, find the In SPI, inCryptoKey and inbound_auth_key for this tunnel. There will be 2 sets of them, one for IPSec SA 1 and another set for IPSec SA 2. For this case, let’s use the keys from IPSec SA 1.
Note: These values are not printed in the TSR on all devices unless sensitive key option is enabled.
3. Copy the values highlighted in the screenshot below:
4. On the Wireshark, navigate to EDIT>PREFERENCES>expand PROTOCOLS and find ESP
5. Check the box ATTEMPT TO DETECT/DECODE ENCRYPTED ESP PAYLOADS and click EDIT
6. Fill the values as shown in below screenshot and click OK.
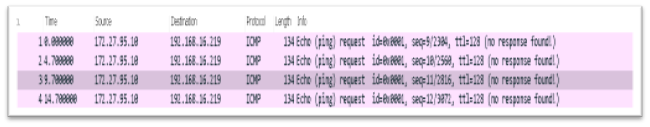
7. After decrypting the ESP packets, we see that the source and the destination are shown as plain text as below:
I hope this information is helpfull.
Stay Safe!!
Regards,
Nevyaditha P
Nevyaditha P
Technical Support Advisor, Premier Services







Comments
@Nevyaditha great stuff, nice piece of infromation, many thanks. 👍️
Here is the KB on this topic.
Thanks!
Shipra Sahu
Technical Support Advisor, Premier Services
Thank you @franz !!! I am glad you liked it :)
Nevyaditha P
Technical Support Advisor, Premier Services